

2017/05/02 Microsoft Cloud Solutions 3859 visit(s)
Ctelecoms

Simply by migrating to Office 365 or submitting your information in the form above to enjoy our FREE 30-DAY Office 365 Business TRIAL which will give you the most powerful tools needed to take full advantage of Multi-factor authentication. The Office 365 administrator has the unique ability to enroll users for multi-factor authentication through the Office 365 admin center. The admin can also configure App Passwords for Office desktop applications.
After a user is enabled for multi-factor authentication, they will be required to configure their second factor of authentication at their next login. Each subsequent login is enforced and will require use of the password and phone acknowledgement.
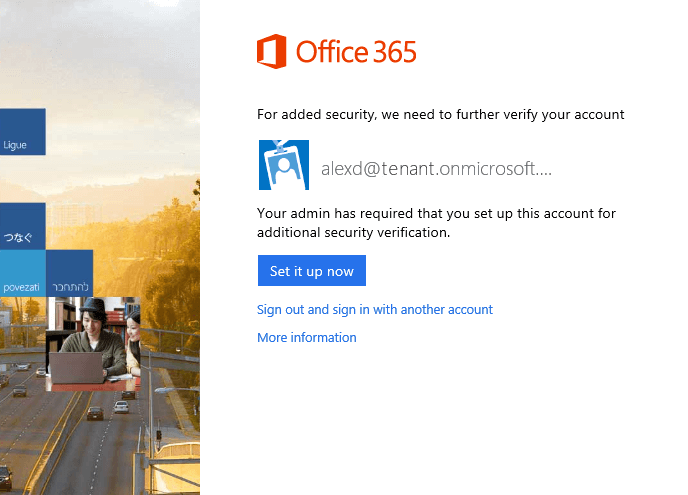
Any of the following may be used for the second factor of authentication
Call my mobile phone
The user receives a phone call that asks them to press the pound key. Once the pound key is pressed, the user is logged in.
Text code to my mobile phone
The user receives a text message containing a six-digit code that they must enter into the portal.
Call my office phone
This is the same as Call my mobile phone, but it enables the user to select a different phone if they do not have their mobile phone with them.
Notify me through app
The user configures a smartphone app and they receive a notification in the app that they must confirm the login. Smartphone apps are available for Windows Phone, iPhone, and Android devices.
Show one-time code in app
The same smartphone app is used. Instead of receiving a notification, the user starts the app and enters the six-digit code from the app into the portal.